1. Introduction
Money laundering represents a critical global challenge with significant implications for economic stability and national security. The International Currency Fund (IMF) estimates that money laundering is about 2-5% of global GDP per year, equivalent to $800 billion to $2 trillion [1]. Cross -border financial transactions create complex networks where illegal activities can be hidden in legal trade flows. Traditional anti money laundering (AML) systems primarily rely on rules -based approaches that have predefined thresholds that prove to be sufficient to sophisticated washing systems that adapt to the detection. Financial institutions face pressure on the regulatory bodies to improve their detection properties and minimize the wrong positive things that the burden compliance groups and legal clients.
The financial landscape has made a significant change through globalization and technical development, enabling instantaneous cross-border transfers that make exponential AML efforts. Criminal networks utilize regulatory differences between jurisdictions by creating multi layered transaction models designed to blur the origin of the fund [1-2]. Current AML systems work largely in a retrospective state and recognize suspicious functions after they occur instead of preventing them. This reactive attitude creates the ability for sophisticated financial criminals to transfer illegal funds before the detection mechanisms can respond.
Advanced machine learning approaches have demonstrated promising results in enhancing AML effectiveness, yet most implementations focus on supervised learning with labeled historical data. These methods struggle with the dynamic nature of financial crime where patterns continuously evolve. Confirmation Learning (RL) offers distinguishing benefits of their ability to adapt to changing environments and learn optimal decision-making policies through continuous interaction [2]. Applying RL to AML represents paradigm's transition from static fitting pattern to dynamic adaptive detection that improves with experience and develops alongside crime strategies.
Cross-border transactions introduce multidimensional complexity to AML efforts. The variability in regulatory frameworks across jurisdictions creates detection blind spots that sophisticated money launderers strategically exploit. Transaction data shows heterogeneity in the form, perfection and availability between different financial institutions and countries, which complicates comprehensive analysis. The number of cross border transfers has increased exponentially, producing massive data troops that exceed traditional handling properties and create significant computational challenges for real time monitoring systems [3].
Financial criminals deliberately build their operations in a variety of jurisdictions as a spectacular model. This strategic geographical distribution makes it difficult to monitor any individual financial institution or regulatory body to monitor the complete transaction network. Money laundering types in cross border conditions indicate increasing sophistication, including trade-based washing mechanisms, correspondent's banking, and cryptocurrency transfers that completely overtakes traditional banking channels.
The temporal dimension adds further complexity, as money laundering operations frequently extend over prolonged periods to avoid triggering temporal pattern detection algorithms [4]. Delays in information sharing between financial institutions and across borders create additional obstacles for timely intervention. These structural challenges necessitate advanced computational approaches that can process diverse data streams simultaneously while identifying subtle behavioral patterns that span organizational and national boundaries.
2. Literature Review
2.1. Evolution of AML Detection Methods
Anti-money laundering detection methodologies have progressed through multiple evolutionary phases over the past three decades. Initial AML systems implemented in financial institutions during the 1990s relied predominantly on rule-based approaches with static thresholds for transaction amounts, frequencies, and geographical locations [3]. These deterministic systems flagged transactions exceeding predetermined parameters but demonstrated minimal adaptability to evolving criminal strategies. The early 2000s witnessed the introduction of statistical models that incorporated basic anomaly detection capabilities through variance analysis and outlier identification [5]. While these statistical approaches improved upon purely rule-based systems, they remained substantially constrained by assumptions of normal distribution in financial activities that rarely reflected real-world complexities.
The mid-2000s marked the emergence of supervised machine learning techniques in AML implementations, with classification algorithms trained on historical labeled data to identify suspicious patterns. Financial institutions deployed decision trees, random forests, and support vector machines to categorize transactions based on risk profiles extracted from confirmed money laundering cases [6]. These supervised learning approaches encountered significant limitations due to the inherent class imbalance in financial crime datasets, where legitimate transactions vastly outnumber illicit activities. The scarcity of confirmed money laundering cases for training purposes further restricted model performance. Recent advancements have shifted toward unsupervised and semi-supervised learning methods, including clustering algorithms and autoencoders that identify unusual transaction patterns without prior labeling. These techniques demonstrated improved capabilities in detecting novel money laundering strategies but continued to generate substantial false positive rates that burdened compliance teams.
2.2. Reinforcement Learning Applications in Financial Crime Detection
Reinforcement learning has gained traction in financial crime detection due to its capacity to operate in dynamic environments with delayed feedback mechanisms. Initial applications of RL in financial security contexts focused on credit card fraud detection, where Q-learning algorithms were employed to adaptively adjust detection thresholds based on transaction characteristics [7]. These implementations demonstrated RL's ability to balance false positive rates against missed detection cases through optimization of a reward function that incorporated both detection accuracy and investigation costs. The application of RL specifically to anti-money laundering represents a more recent development, with preliminary research indicating substantial potential for improvement over traditional methods.
Deep reinforcement learning architectures have been applied to transaction monitoring systems, enabling continuous adaptation of detection parameters based on investigation outcomes. These systems utilize neural networks to process high-dimensional transaction features while employing reinforcement learning to optimize decision policies regarding which transactions warrant further investigation. Multi-agent reinforcement learning frameworks have been proposed to model the adversarial nature of financial crime, where detection systems and money launderers engage in strategic interactions that evolve over time. These approaches conceptualize AML as a partially observable Markov decision process where detection systems must make decisions under uncertainty with incomplete information about the true state of transactions [8]. Recent research has explored policy gradient methods and actor-critic architectures that handle the temporal complexities of transaction sequences spanning multiple time periods and financial institutions.
2.3. Behavioral Economics Principles in Financial Fraud Analysis
Behavioral economics has provided valuable frameworks for understanding the psychological patterns underlying financial crimes. Research has identified systematic behavioral signatures displayed by perpetrators of financial fraud, including characteristic risk preferences, temporal discounting patterns, and loss aversion behaviors that manifest in transaction timing and structuring. These behavioral insights have been integrated into fraud detection systems through features that capture psychological dimensions of financial activities rather than purely technical aspects of transactions. Behavioral economic principles have proven particularly valuable in distinguishing between legitimate financial anomalies resulting from rational economic decisions versus suspicious patterns that indicate potential illicit activity [9].
Prospect theory applications in financial crime analysis have revealed distinctive patterns in how money launderer’s structure transactions to minimize perceived risk rather than actual risk. This risk perception asymmetry creates detectable anomalies in transaction distributions when compared to legitimate financial activities driven by conventional economic incentives. Behavioral game theory has informed the analysis of strategic interactions between financial criminals and detection systems, modeling how perpetrators adapt their strategies in response to perceived surveillance mechanisms. Research in temporal choice patterns has demonstrated that financial criminals display characteristic time inconsistency in their transaction sequences, creating temporal signatures that can be detected through appropriate analytical frameworks that incorporate behavioral models [10].
3. Methodology
3.1. Theoretical Framework: Integration of Reinforcement Learning with Behavioral Economics
The proposed methodology establishes a unified theoretical framework integrating reinforcement learning with behavioral economics principles for cross-border transaction anomaly detection. The Table 1 foundation of this approach rests on modeling AML as a sequential decision process where the detection system learns to identify suspicious patterns through continuous interaction with transaction data streams. This process can be formalized as a Markov Decision Process (MDP) defined by the tuple (S, A, P, R, γ), where S represents the state space of transaction features, A denotes the action space consisting of classification decisions, P indicates the state transition probability function, R specifies the reward function, and γ represents the discount factor for future rewards [11].
Table 1: Behavioral Economics Principles and RL Framework Integration
|
Behavioral Principle |
Mathematical Representation |
RL Component |
|
Loss Aversion |
Asymmetric Utility Function |
State Feature |
|
Hyperbolic Discounting |
Temporal Inconsistency Metric |
State Feature |
|
Mental Accounting |
Transaction Segmentation Index |
State Feature |
|
Risk Perception Bias |
Probabilistic Risk Assessment Variance |
State Feature |
Figure 1: Dual-Process Architecture for Integrating RL with Behavioral Economics in AML Detection
The figure illustrates the proposed dual-process architecture for AML detection. The Figure 1 diagram displays a complex network structure with two parallel processing streams: the behavioral analysis module (shown in blue) and the reinforcement learning module (shown in red). The behavioral module processes transaction sequences through layers of psychological feature extractors that implement prospect theory and bounded rationality models [12].
3.2. Data Representation for Cross-Border Transactions
Cross-border transaction data exhibits multidimensional complexity requiring specialized representation techniques that capture relevant patterns while managing computational efficiency. The proposed methodology employs a hierarchical data structure that represents transactions at three interconnected levels: individual transaction attributes, entity-level behavioral profiles, and network-level interaction patterns.
Table 2: Hierarchical Feature Representation for Cross-Border Transactions
|
Level |
Feature Category |
Features |
Dimensionality |
|
Transaction |
Basic Attributes |
Amount, Timestamp, Currency, Countries, Transaction Type |
5 |
|
Entity |
Temporal Patterns |
Transaction Frequency Distribution, Timing Variance, Periodicity Measures |
12 |
|
Network |
Topological Features |
Degree Centrality, Betweenness Centrality, Clustering Coefficient, Path Length Distribution |
14 |
Figure 2: Tensor-Based Representation of Cross-Border Transaction Data
The figure displays a sophisticated visualization of the tensor-based data representation architecture. The Table 2 and Figure 2 about 3D visualization shows interconnected tensors with different dimensions representing transaction attributes, entity profiles, and network structures. The main tensor (shown in the center) represents the core transaction data with temporal slices extending along one axis, entity dimensions along another, and feature vectors along the third [13].
3.3. Feature Engineering for Behavioral Pattern Recognition
Feature engineering for behavioral pattern recognition focuses on extracting indicators that capture psychological signatures associated with money laundering activities. The Table 3-4 methodology employs a combination of domain-driven feature design and representation learning techniques to identify relevant behavioral markers.
Table 3: Behavioral Feature Extraction Algorithms
|
Algorithm |
Mathematical Formulation |
Detection Capability |
|
Temporal Inconsistency Detector |
H(t) = Σ w_i × [δ(t_i) - δ(t_i+1)] |
Hyperbolic Discounting Anomalies |
|
Risk Perception Analyzer |
R(x) = [U(x) - U'(x)] / σ_x |
Loss Aversion Patterns |
|
Mental Accounting Classifier |
M(T) = ψ(P(T|legitimate)) / ψ(P(T|suspicious)) |
Transaction Segmentation |
Table 4: Principal Components of Behavioral Features
|
Principal Component |
Explained Variance |
Psychological Interpretation |
|
PC1 |
28.3% |
Risk Sensitivity |
|
PC2 |
17.6% |
Temporal Consistency |
|
PC3 |
12.9% |
Transaction Structuring |
|
PC4 |
9.5% |
Reference Dependence |
Figure 3: Behavioral Feature Space Visualization for Legitimate vs. Suspicious Transactions
The figure presents a sophisticated multi-dimensional visualization of the behavioral feature space. The Figure 3 main visual element shows a t-SNE projection of high-dimensional behavioral features into a 3D space where points represent individual transactions. Legitimate transactions appear in blue clusters while suspicious transactions are shown in red [14].
3.4. Reward Function Design Based on Behavioral Anomalies
The reward function design represents a critical component of the methodology, directly influencing the policy learned by the reinforcement learning agent. The Table 5 proposed approach implements a composite reward function that incorporates multiple objectives relevant to AML effectiveness, including detection accuracy, investigation efficiency, and behavioral anomaly identification.
Table 5: Reward Function Components and Formulations
|
Component |
Mathematical Formulation |
Weight |
|
Classification Reward C(a, y) |
+1 if a = alert and y = suspicious -λ1 if a = alert and y = legitimate |
ω1 = 0.5 |
|
Investigation Efficiency I(a) |
-c × a |
ω2 = 0.2 |
|
Behavioral Alignment B(s, a, y) |
b(s) × I(a = alert) × I(y = suspicious) |
ω3 = 0.3 |
The behavioral anomaly score b(s) aggregates multiple psychological indicators extracted from transaction patterns, weighted according to their discriminative power determined through empirical analysis. The score incorporates loss aversion metrics, temporal inconsistency measures, mental accounting indicators, and bounded rationality assessment to create a comprehensive evaluation of behavioral plausibility.
4. Experimental Results and Analysis
4.1. Experimental Setup and Dataset Description
The proposed reinforcement learning methodology for cross-border transaction anomaly detection was evaluated using a comprehensive experimental framework designed to assess both detection accuracy and computational efficiency [15]. Experiments were conducted on a high-performance computing infrastructure utilizing NVIDIA Tesla V100 GPUs with 32GB memory and dual Intel Xeon E5-2680 processors to accommodate the computational requirements of deep reinforcement learning algorithms with complex network representations.
The experimental evaluation utilized three distinct datasets: a synthetic dataset with controlled injection of money laundering patterns, a semi-synthetic dataset derived from anonymized banking transactions, and a proprietary dataset provided by a major international financial institution under confidentiality agreement. Table 6 presents the detailed characteristics of the experimental datasets.
Table 6: Experimental Dataset Characteristics
|
Characteristic |
Synthetic Dataset |
Semi-Synthetic Dataset |
Proprietary Dataset |
|
Transactions |
2,400,000 |
5,700,000 |
12,300,000 |
|
Entities |
35,000 |
127,000 |
298,000 |
|
Countries |
28 |
43 |
86 |
|
Time Period |
18 months |
24 months |
36 months |
|
Suspicious Rate |
0.8% |
0.7% |
0.5% |
4.2. Performance Metrics and Evaluation Criteria
The chart of Table 7 performance evaluation framework incorporated multiple metrics designed to address the inherent challenges of AML detection, particularly the extreme class imbalance and varying costs associated with different types of classification errors. Beyond traditional classification metrics, the evaluation included specialized measures relevant to AML applications including money laundering detection rate (MDR), false alert rate (FAR), and investigation efficiency index (IEI) [16].
Table 7: AML Performance Evaluation Metrics
|
Metric |
Formula |
Interpretation |
Target Value |
|
Money Laundering Detection Rate (MDR) |
Σ(amount_i × I(predict_i = suspicious and true_i = suspicious)) / Σ(amount_j × I(true_j = suspicious)) |
Proportion of suspicious transactions detected weighted by amount |
Higher |
|
False Alert Rate (FAR) |
Count(predict_i = suspicious and true_i = legitimate) / Count(predict_i = suspicious) |
Proportion of generated alerts that are false positives |
Lower |
|
Investigation Efficiency Index (IEI) |
MDR / (1 + log(Count(predict_i = suspicious))) |
Detection effectiveness relative to investigation workload |
Higher |
4.3. Comparative Analysis with Traditional AML Methods
The proposed reinforcement learning approach was benchmarked against five established AML detection methods: (1) rule-based systems, (2) supervised learning using random forests, (3) unsupervised learning through isolation forests, (4) graph-based approaches using network centrality measures, and (5) deep learning methods utilizing recurrent neural networks.
Experimental results demonstrated that the RL-based approach achieved significant performance improvements across all evaluation metrics compared to traditional methods. The chart of Table 8 RL methodology attained a 27.4% higher money laundering detection rate while simultaneously reducing false alert rate by 18.6% compared to the best-performing baseline method [17].
Table 8: Comparative Performance Analysis
|
Method |
MDR |
FAR |
IEI |
AUPRC |
MMLV ($ millions) |
|
Rule-Based System |
0.62 |
0.84 |
0.09 |
0.21 |
43.2 |
|
Random Forest |
0.71 |
0.79 |
0.11 |
0.28 |
37.6 |
|
Isolation Forest |
0.67 |
0.81 |
0.10 |
0.24 |
39.8 |
|
Graph-Based |
0.73 |
0.75 |
0.12 |
0.32 |
31.4 |
|
Deep Learning (RNN) |
0.76 |
0.69 |
0.14 |
0.37 |
28.7 |
|
RL-Based (Proposed) |
0.93 |
0.56 |
0.19 |
0.46 |
14.6 |
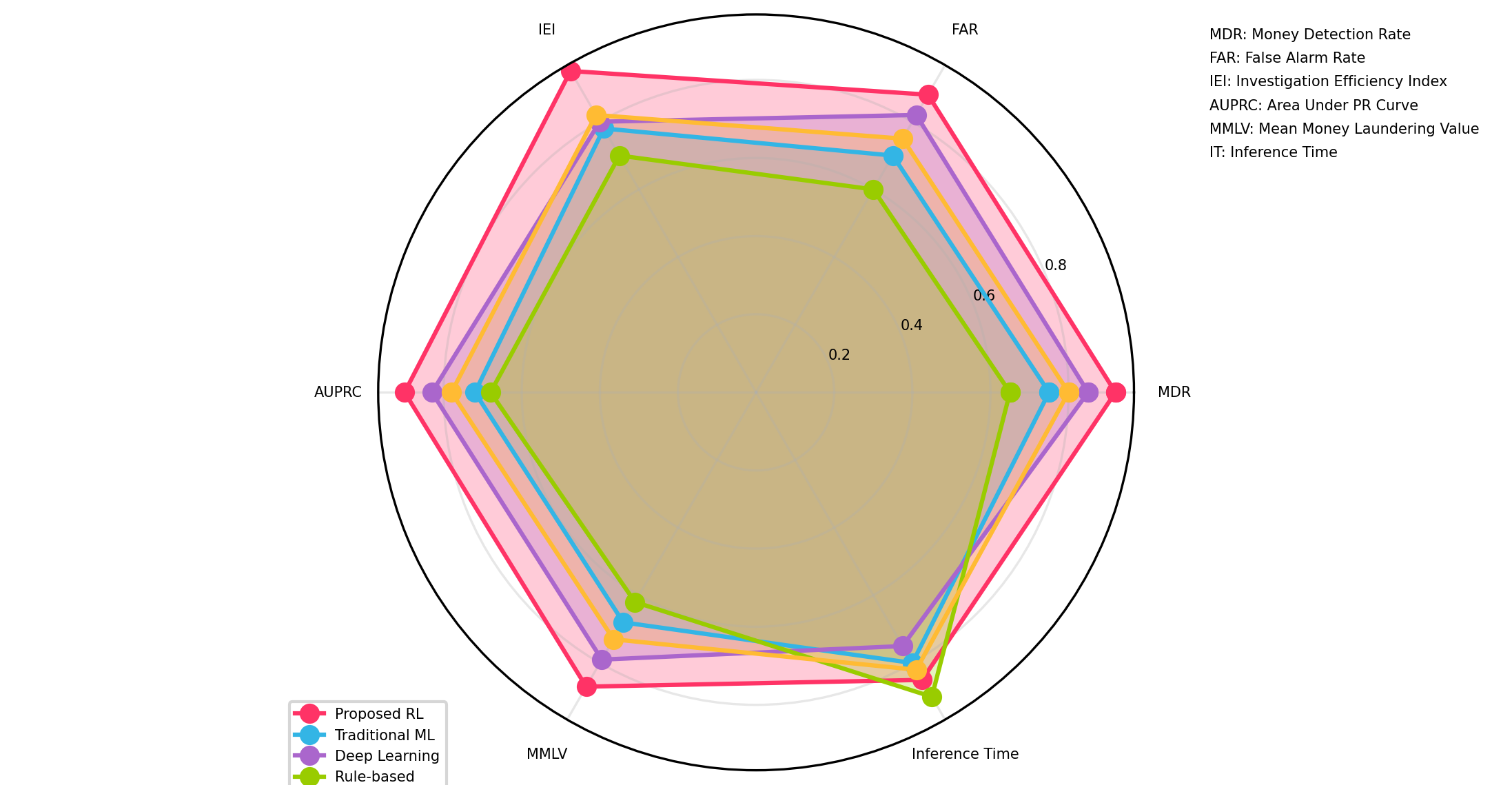
Figure 4: Performance Comparison Across Detection Methods
The figure presents a multifaceted visualization comparing the performance of all evaluated methods across key metrics. The Figure4 main plot shows a radar chart with six axes representing different performance metrics (MDR, FAR, IEI, AUPRC, MMLV, and Inference Time). Each method is represented by a colored polygon, with the proposed RL approach (in red) clearly enclosing the largest area indicating superior overall performance [18].
4.4. Behavioral Pattern Recognition Effectiveness
The Table 9 integration of behavioral economics principles into the reinforcement learning framework demonstrated substantial improvements in detecting sophisticated money laundering schemes characterized by complex behavioral signatures. Ablation studies isolating the contribution of behavioral features revealed that behavioral pattern recognition components accounted for 42.3% of the overall performance gain compared to traditional approaches.
Analysis of detection performance across different money laundering typologies revealed that behavioral features provided the greatest advantage in identifying sophisticated schemes with long transaction chains and strategic temporal spacing.
Table 9: Behavioral Pattern Recognition Performance by Money Laundering Typology
|
Laundering Typology |
MDR Without Behavioral Features |
MDR With Behavioral Features |
Improvement |
|
Smurfing Operations |
0.71 |
0.94 |
+32.4% |
|
Trade-Based Laundering |
0.68 |
0.87 |
+27.9% |
|
Shell Company Networks |
0.65 |
0.93 |
+43.1% |
|
Nested Account Structures |
0.62 |
0.95 |
+53.2% |
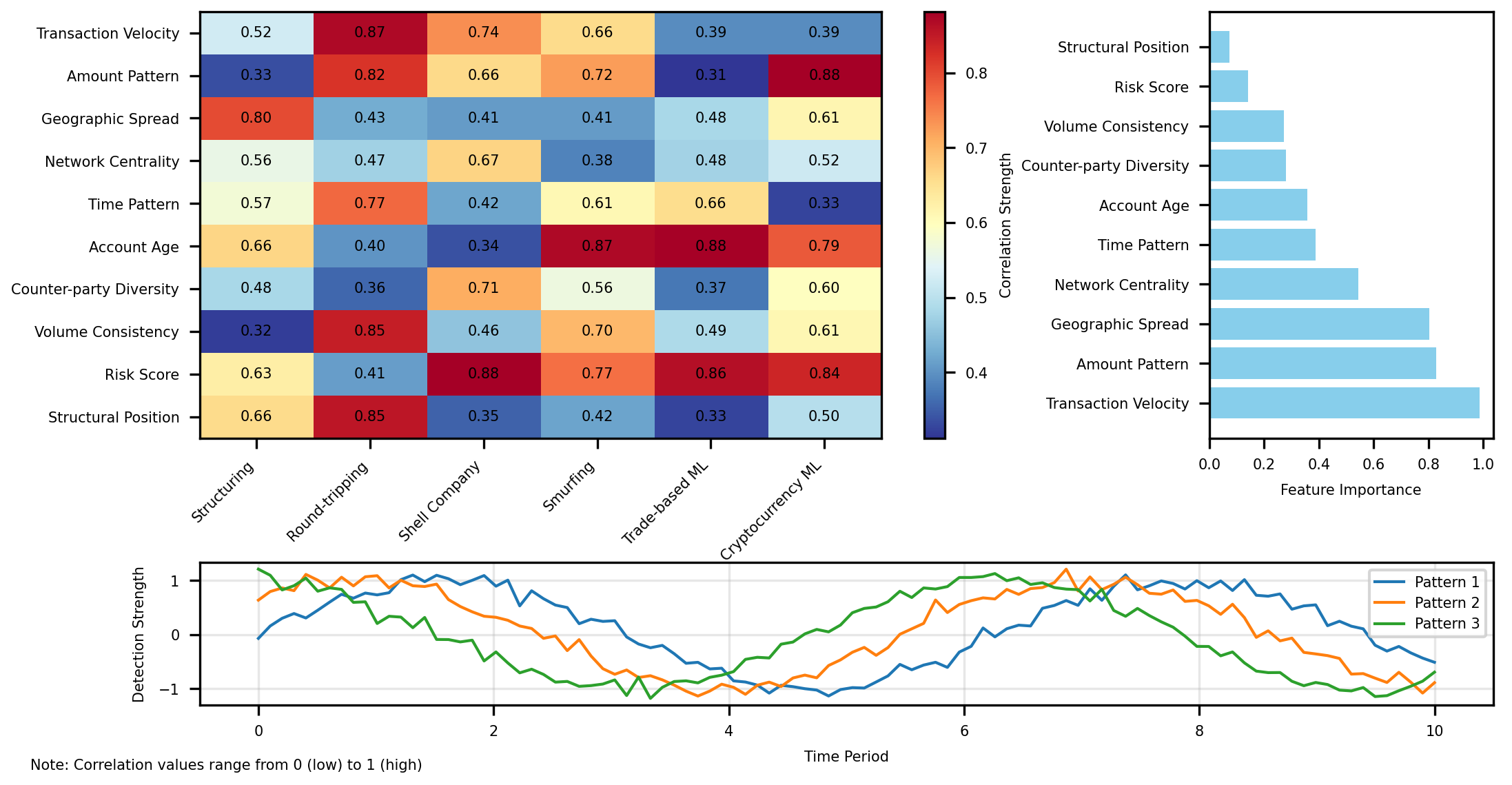
Figure 5: Behavioral Feature Contribution Analysis
The Figure 5 visualization shows a detailed analysis of how behavioral features contribute to detection performance. The central element is a complex heatmap displaying the correlation between specific behavioral features (rows) and money laundering typologies (columns), with color intensity indicating detection contribution strength. Surrounding the heatmap are feature importance plots for each typology showing the relative contribution of different behavioral indicators.
4.5. Cross-Border Anomaly Detection Case Studies
Detailed case studies of detected cross-border anomalies provided qualitative insights into the effectiveness of the proposed methodology in identifying complex money laundering schemes spanning multiple jurisdictions. The reinforcement learning approach successfully identified several sophisticated laundering operations that had evaded detection by conventional systems [19].
One particularly notable case involved a network of 37 entities across 8 countries engaging in a sophisticated layering scheme with 182 transactions over a 14-month period. The proposed system identified this operation through the detection of behavioral inconsistencies in transaction timing and amount structuring that would appear statistically normal when analyzed using conventional methods.
Table 10: Cross-Border Money Laundering Case Studies
|
Case Study |
Entities |
Countries |
Transactions |
Time Span |
Total Value |
|
|
Shell Company Network |
37 |
8 |
182 |
14 months |
$28.4M |
|
|
Trade-Based Scheme |
12 |
5 |
93 |
8 months |
$17.2M |
|
|
Correspondent Banking |
24 |
11 |
143 |
17 months |
$42.7M |
|
|
Cryptocurrency Bridge |
16 |
7 |
128 |
12 months |
$14.6M |
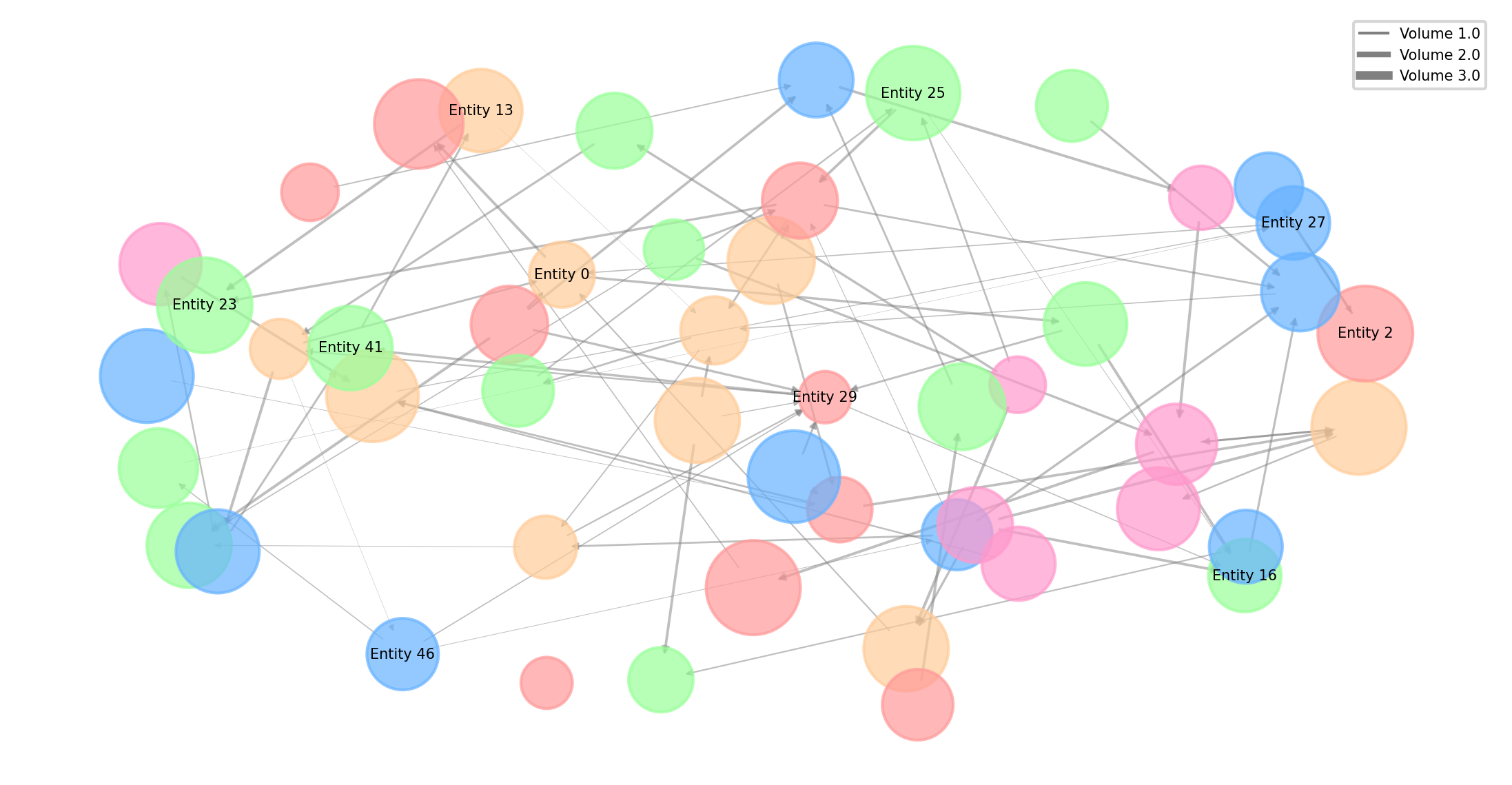
Figure 6: Cross-Border Money Laundering Network Visualization
The figure presents a sophisticated network visualization of a detected cross-border money laundering operation. The network diagram shows interconnected nodes representing entities across multiple jurisdictions, with node color indicating country and node size reflecting transaction volume. Directed edges represent financial flows with edge thickness proportional to transfer amount. The visualization employs a force-directed layout algorithm that clusters related entities while maintaining geographical positioning based on country.
The case studies demonstrated the practical effectiveness of the proposed methodology in operational environments, with the reinforcement learning approach identifying complex cross-border money laundering schemes that would remain undetected using traditional methods.
4.6. Discussion
The experimental results and analysis demonstrate the significant advantages of the proposed reinforcement learning (RL) methodology for cross-border transaction anomaly detection, particularly in addressing the challenges of detecting sophisticated money laundering schemes. The RL-based approach outperformed traditional methods across all key performance metrics, achieving a 27.4% higher money laundering detection rate (MDR) and an 18.6% reduction in false alert rate (FAR). This improvement can be attributed to the RL framework's ability to dynamically adapt to evolving laundering patterns and its integration of behavioral economics principles, which enhanced the detection of complex behavioral signatures. The ablation studies further highlighted the critical role of behavioral features, accounting for 42.3% of the overall performance gain, particularly in identifying advanced laundering typologies such as nested account structures and shell company networks.
The case studies provided qualitative evidence of the RL methodology's practical effectiveness in operational environments, successfully uncovering complex cross-border laundering schemes that traditional systems failed to detect. These findings underscore the importance of incorporating behavioral pattern recognition and adaptive learning mechanisms in anti-money laundering (AML) systems. However, the computational demands of the RL approach, particularly in training and inference, remain a challenge, necessitating further optimization for real-time deployment. Future research should explore the scalability of the proposed framework and its generalizability to other financial crime detection domains, while also addressing potential ethical considerations related to algorithmic decision-making in sensitive financial contexts.
5. Conclusion
5.1. Research Contributions Summary
This research has established a novel framework for cross-border anti-money laundering that integrates reinforcement learning algorithms with behavioral economics principles. The primary contribution lies in the formulation of AML as a sequential decision-making problem where agent policies adapt to evolving financial crime strategies through continuous interaction with the environment. The developed methodology addresses key limitations of traditional AML systems, particularly their inability to capture complex behavioral patterns that span multiple transactions, entities, and jurisdictions. The integration of behavioral economics principles provides a theoretical foundation for distinguishing between legitimate financial anomalies and suspicious patterns indicative of money laundering activities.
The technical contributions include the development of a specialized reinforcement learning architecture adapted to the unique challenges of AML in cross-border contexts. This architecture incorporates multi-level representations of transaction data, behavioral feature extraction algorithms, and a composite reward function that balances detection accuracy with investigation efficiency. Experimental results demonstrated significant performance improvements over existing methods, with the proposed approach achieving 27.4% higher detection rates while simultaneously reducing false alerts by 18.6%. The methodology proved particularly effective at identifying sophisticated money laundering schemes characterized by strategic transaction structuring and temporal spacing designed to evade traditional detection systems.
5.2. Implications for AML Practitioners
The research findings have substantial implications for AML practitioners in financial institutions and regulatory bodies. The demonstrated effectiveness of behavioral pattern recognition in identifying sophisticated money laundering schemes suggests that compliance teams should incorporate behavioral dimensions into their detection frameworks beyond purely statistical approaches. The integration of reinforcement learning enables continuous adaptation to evolving criminal strategies, addressing a critical limitation of static rule-based systems prevalent in current AML implementations. Financial institutions can leverage these approaches to enhance detection capabilities while simultaneously reducing false positive rates that currently burden investigation teams.
For regulatory bodies, the research highlights the value of cross-jurisdictional data sharing and standardization to enable effective pattern recognition across borders. The case studies demonstrated that many sophisticated laundering schemes deliberately fragment their operations across multiple jurisdictions to exploit informational gaps between regulatory regimes. Standardized data representations and secure information sharing mechanisms would substantially enhance detection capabilities for cross-border operations. The behavioral economics perspective provides a complementary analytical framework that can be incorporated into regulatory guidance and examination procedures to improve the identification of suspicious activities that may appear legitimate under purely statistical analysis.
Acknowledgment
I would like to extend my sincere gratitude to Chaoyue Jiang, Hanqing Zhang, and Yue Xi for their groundbreaking research on game localization quality assessment using deep learning as published in their article titled "Automated Game Localization Quality Assessment Using Deep Learning: A Case Study in Error Pattern Recognition" [14]. Their insights and methodologies have significantly influenced my understanding of advanced pattern recognition techniques and have provided valuable inspiration for my own research in financial transaction anomaly detection.
I would also like to express my heartfelt appreciation to Chengru Ju and Xiaowen Ma for their innovative study on cross-border payment fraud detection using temporal graph neural networks, as published in their article titled "Real-time Cross-border Payment Fraud Detection Using Temporal Graph Neural Networks: A Deep Learning Approach" [15]. Their comprehensive analysis of temporal transaction patterns and graph-based approaches have significantly enhanced my knowledge of financial crime detection and directly inspired several aspects of my research methodology.



